ImageMagick MSIX is Now Built and Signed with Trusted Signing via Advanced Installer
The ImageMagick team has recently adopted Trusted Signing to enhance the security and reliability of its binaries and installers.
You might be wondering why we are suddenly using a new product called Trusted Signing.
The reason is simple: Azure Code Signing is now called Trusted Signing.
The configuration inside Azure hasn't changed, and we are still using the same certificate profile to sign the binaries and the installer. The only thing that has changed is the name of the product. This change was made right before the Public Preview of this product.
We are now using this together with Advanced Installer to build and sign the new MSIX installer for ImageMagick, simplifying the installation process on Windows systems.
How can I use Trusted Signing?

Trusted Signing, now available in Public Preview, can be accessed via the Azure Portal.
Here’s how you can get started:
1. Open Azure Portal: Search for “trusted” to locate the Trusted Signing Accounts page.

2. Create a New Account: Follow the instructions to set up your Trusted Signing account.

For a detailed setup guide, you can follow the instructions provided in the article: ImageMagick now uses Azure Code Signing.
Why a New MSIX Installer?

We created a new MISX installer to simplify the installation process of ImageMagick on Windows machines.
The new MSIX installer, built similarly to our portable releases, does not use the Windows registry.
This setup facilitates future publishing on the Microsoft Store, although currently, it is available on WinGet. This will allow users to install ImageMagick using a single command:
winget install ImageMagick.Q16-HDRI
Creating the MSIX Installer with Advanced Installer

The MSIX installer was created using Advanced Installer, a versatile tool for creating various installer types.
Our configuration file for the project is available here: https://github.com/ImageMagick/ImageMagick-Windows/blob/main/Installer/Msix/ImageMagick.Q16-HDRI.aip.
Advanced Installer made the configuration straightforward, requiring minimal adjustments to create the installer.
Advanced Installer also supports creating an .msixbundle, containing both x64 and the arm64 binaries, ensuring the correct architecture is installed for the user. We opted not to include an x86 build because most users will no longer need this.
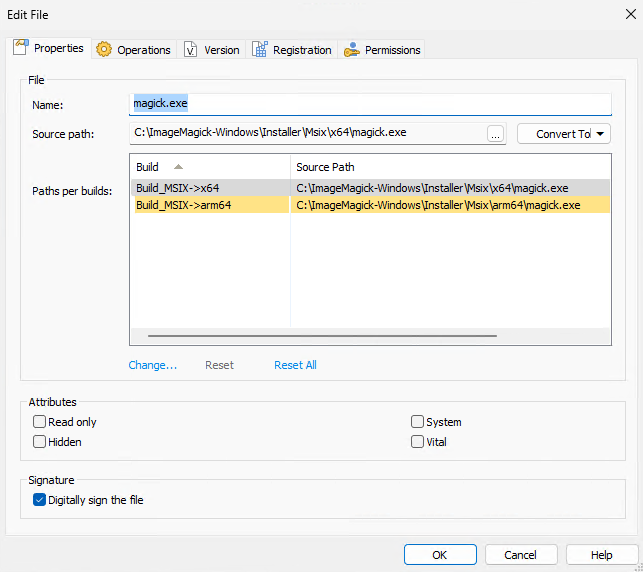
Another great feature we leveraged is the bundling of only magick.exe in the installer.
The installer creates other aliases that are available in the portable release (e.g., identify.exe, mogrify.exe) automatically.
Our magick.exe file checks on startup what the name of the application is and chooses a different flow depending on the name of the program. Having only one executable reduces both the installer size and the file footprint on users' machines.

Signing the MSIX Installer with Advanced Installer's Built-In Support for Trusted Signing

Signing the installer is integrated within Advanced Installer’s GUI.
By enabling the "Use Trusted Signing" option, we sign the installer with a Trusted Signing certificate. This ensures that the installer won't show a warning when users try to install it and will clearly indicate that it is signed by ImageMagick.

Since we use Trusted Signing, we also need to set some environment variables to build the installer. The environment variables AZURE_CLIENT_ID, AZURE_TENANT_ID, and AZURE_CLIENT_SECRET are used by signtool to authenticate in Azure and to sign the installer, as well as the .dll and .exe files included in it.

Integration with ImageMagick’s Continuous Integration System Using Advanced Installer

Advanced Installer provides a GitHub action for building the installer, which we use in ImageMagick’s CI.
This action can be found here: https://github.com/Caphyon/advinst-github-action.
The following example shows how we use this action:
- jobs:
- windows:
name: 'Windows'
runs-on: windows-latest
# This is required for the federated credential to work
permissions:
id-token: write
contents: read # This is required for a check out of the repository
steps:
# Build our binaries...
- name: 'Azure CLI login with federated credential'
uses: azure/login@v2
with:
client-id: ${{ secrets.AZURE_CLIENT_ID }}
tenant-id: ${{ secrets.AZURE_TENANT_ID }}
subscription-id: ${{ secrets.AZURE_SUBSCRIPTION_ID }}
- name: Create msixbundle with Advanced Installer
if: github.event_name != 'pull_request'
uses: caphyon/advinst-github-action@v2.0
with:
advinst-license: ${{ secrets.ADVINST_LICENSE_KEY }}
aip-path: ImageMagick-Windows\Installer\Msix\ImageMagick.Q16-HDRI.aip
aip-build-name: Build_MSIX
aip-commands: |
SetVersion ${{ needs.version.outputs.version }}This action builds and signs the installer using the certificate configured in the Advanced Installer project file. After that, the installer is uploaded to ImageMagick's GitHub release page.
The advantage of this setup is that we only need to configure the Advanced Installer action, without needing a separate action to sign the installer and the .dll and .exe files included in it.
In the example above, we’re using federated credentials and you can find more information on how to set this up in the article: ImageMagick now uses Azure Code Signing.
Downloading the MSIX Installer

You can find the new installer ImageMagick's GitHub releases page.
Check out the latest release here: https://github.com/ImageMagick/ImageMagick/releases.
For now, we only support a Q16-HDRI build, but we will be going to add Q16 and Q8 builds in the future.
Future of the MSIX Installer

We will not replace the existing installer, as it includes features that are not available in the MSIX installer.
The old installer uses the Windows registry, which is needed for some applications that use ImageMagick.
Conclusion

The introduction of Trusted Signing and the new MSIX installer significantly improves the ease and security of installing ImageMagick on Windows.
Using Advanced Installer has streamlined the process, making the software more accessible and secure. Advanced Installer's robust features have allowed us to create a versatile and efficient installer, ensuring that users have a smooth installation experience.
Get in Touch

For more updates and insights on my work and development projects, follow me on X @MagickNET and connect with me on LinkedIn.
