How To Disable Registry and File Redirections for MSIX
Recently, in one of our previous articles, we covered how MSIX redirects user data to specific locations.
In this article, we will go through the steps needed to disable both file and registry redirections, and the possible challenges or limitations that may arise when we pursue this action.
The registry is virtualized inside the MSIX, and user data from %localappdata% and %appdata% is automatically redirected to %localappdata%\packages\PublisherName.AppName_hash\LocalCache .
File and registry redirections for MSIX are already turned on by default.
Although the redirection is always on, there is a way to disable it in case we need to.
Disabling registry and file redirection


As described in our MSIX introduction guide, most package settings and behaviors are stored in the AppxManifest.xml.
To disable the file and registry redirections, the following properties must be added in the AppxManifest.xml:
- desktop6:RegistryWriteVirtualization: Indicates whether virtualization for the registry is enabled for the desktop application.
- desktop6:FileSystemWriteVirtualization: Indicates whether virtualization for the file system is enabled for the desktop application.
The above properties should be included inside the
Properties element from the manifest.
For
example:
<Properties>
<desktop6:FileSystemWriteVirtualization>disabled</desktop6:FileSystemWriteVirtualization>
<desktop6:RegistryWriteVirtualization>disabled</desktop6:RegistryWriteVirtualization>
</Properties>
However, in order for these properties to work, a
required restricted capability named
unvirtualizedResources must also be added to the
manifest.
This restricted capability can be added in the manifest within the Capabilities element:
<Capabilities><rescap:Capability Name="unvirtualizedResources" /></Capabilities>
What are the limitations when disabling file and registry
redirection?

Unfortunately, when a restricted capability is added and a normal installation is attempted, you will get a "Cannot open app package" error:

Currently, only certain Microsoft store products, such as games, use these restricted capabilities properties. Keep in mind that AppInstaller does not support installing applications with restricted capabilities at this time.
If you add these capabilities and try to publish your app in the
Microsoft Store, chances are that it will get rejected. In order for an
app to be pushed to the store with restricted capabilities, there must
be specific reasons to support why it is needed.
However, there's a workaround that we discovered for installing an MSIX with restricted capabilities: You can run PowerShell as an administrator and use the Add-AppxPackage cmdlet, which we covered in this article .
Disable file redirections with Advanced Installer

If you’re new to Advanced Installer, we
recommend you take advantage of the 30-Day Full-Featured Free Trial (no
credit card required).
Start free trial
For demonstration purposes, we created a simple executable that writes a registry key to HKEY_CURRENT_USER\SOFTWARE\TestReg.
We then created a simple MSIX project in which we added the executable and defined it in the Application Details tab.
To edit the manifest and disable both file and registry redirections:
1. Navigate to the Manifest Editor Page
2. Right-click the Properties element and select New Element
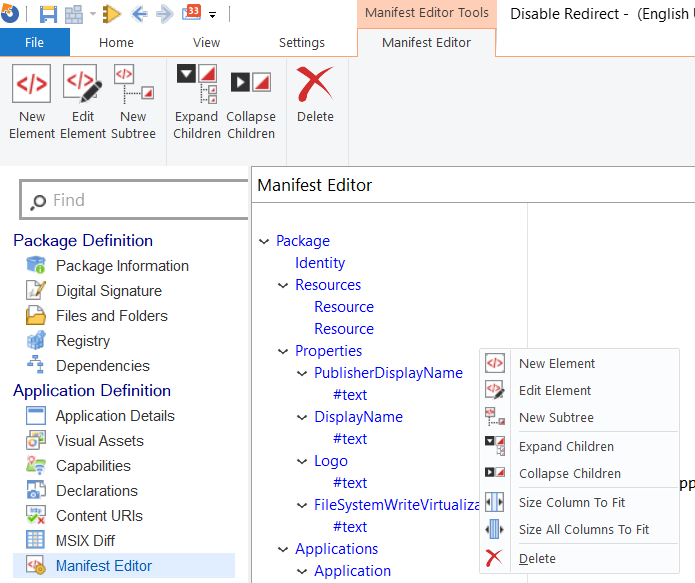
3. In the New Element dialog box, input RegistryWriteVirtualization in the Name field, and disable in the Content field
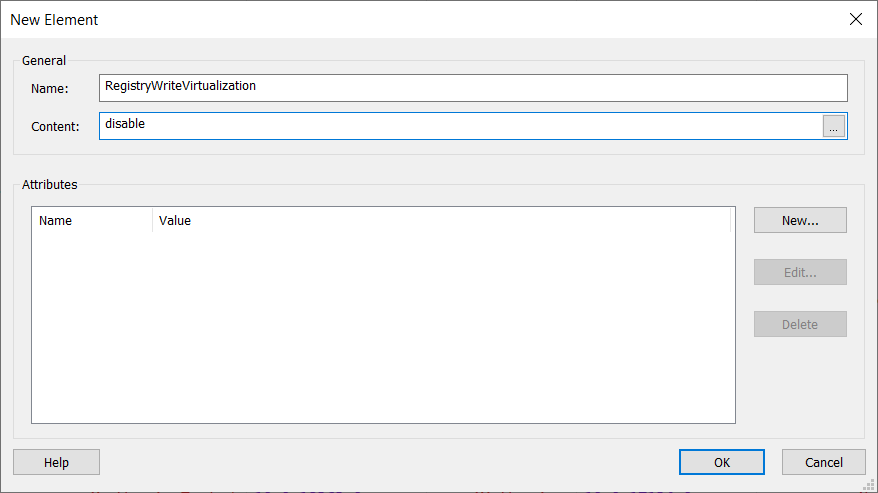
4. Click OK
5. Repeat the same steps for FileSystemWriteVirtualization to disable the file redirection
6. Right-click the Capabilities element and select New Element
7. In the Edit Element dialog box, input Capability in the Name field
8. In the Attributes section, click on New
9. In the Edit Attribute dialog box, input Name in the Name field, and unvirtualizedResources in the Value field
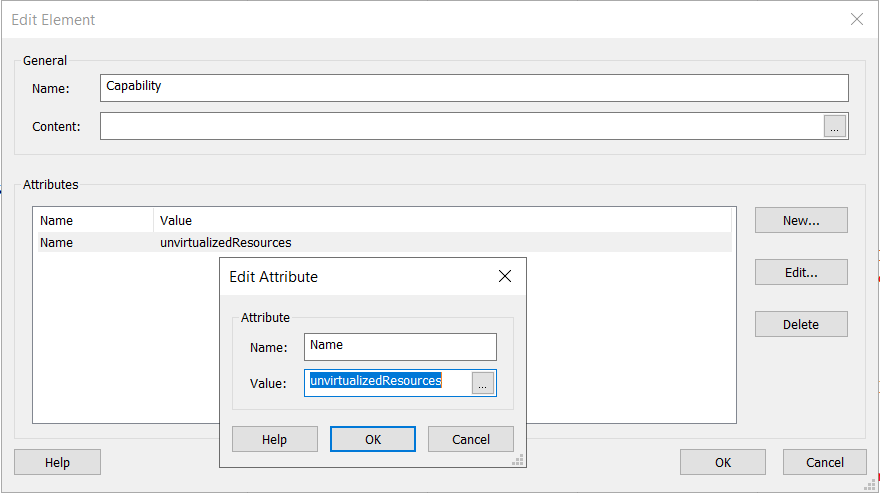
10. Click OK to close the Edit Attribute dialog
11. Click OK to close the Edit Element dialog
With these few easy steps, the AppxManifest.xml will be edited and the MSIX package file and registry redirection will be turned off.
After the app build is configured and the package is signed, we can then create the package and install it.
As previously stated, to install an MSIX with restricted capabilities, we used the Add-AppxPackage cmdlet from a PowerShell with Administrative capabilities.
Upon running the installed application, we will see that our test registry is created outside of the MSIX container, which is exactly the result we expected.

Conclusion

Disabling redirections can be seen as something intended for extremely rare cases, where the package cannot work unless redirections are disabled.
Implementing any restricted capabilities will most likely lead to a Store denial of your package.
If the package is intended only for managed infrastructures, the only downside comes with the install mechanism that must be implemented.
However, keep in mind that during the uninstall, the created registry or files will remain on the machine. MSIX offers clean up only for the redirected files and registry.
Subscribe to Our Newsletter
Sign up for free and be the first to receive the latest news, videos, exclusive How-Tos, and guides from Advanced Installer.