PowerShell & Intune, Automate your Work - Part 1: Retrieve Win32 Apps
PowerShell is a flexible tool created to help in automating your tasks in any environment. The same scenario applies to Intune, where users can use PowerShell extensively to accomplish this.
In this article, we'll explore two important PowerShell modules: AZ and Microsoft Graph, which includes Microsoft.Graph.Authentication.
We'll also go over how Azure authentication works and how to use everything mentioned above to get a list of Win32 applications from Intune via PowerShell.
PowerShell Is Your Key to Mastering Azure

Azure does provide a web interface through which you can manage everything related to your tenant.
Azure is a vast library that allows you to do almost anything related to computing, including hosting websites and applications, managing infrastructure, and analyzing large data models.
PowerShell is now available in all Azure environments, offering many functions as well as the ability to communicate directly with Azure.
I can think of a few examples, such as creating a virtual machine or setting up full networks. All with a few simple lines of text.
If you’re new to PowerShell and need help understanding the core basics, cmdlets, queries, local OS changes, WMI, and more, I recommend the PowerShell for Beginners free eBook.
However, before we use PowerShell with Azure, we need to set up the right tools, specifically the Azure PowerShell module.
The Azure PowerShell module is a collection of cmdlets designed specifically to manage Azure resources directly from the PowerShell command line. Let’s install it.
Getting Started with the AZ Module

In summary, the AZ module is a collection of commands (also referred to as cmdlets in the PowerShell world) created specifically for Azure resource management. This module is very simple to install.
First, you need a recent version of Windows. Windows 10 and 11 will work just fine because PowerShell usually comes preinstalled.
Next on the list is to launch a PowerShell window with admin rights:
- Open the Start Menu
- Type “PowerShell,” right-click on it
- Select “Run as administrator”
With PowerShell running as admin, we can now install the AZ module with the following command:
Install-Module -Name Az -AllowClobber
Where:
- The Install-Module is a popular PowerShell cmdlet which installs any type of module found online
- Az is the name of the Azure model
- -AllowClobber is simply a safety measure that ensures that if there are any conflicts with the existing commands, the new module will take priority
After you click Enter, the system will start downloading the AZ module. Be patient, as this will take a moment.

We recommend checking to make sure everything is in place and running the following command to see all the AZ-related cmdlets:
Get-Module -ListAvailable Az*
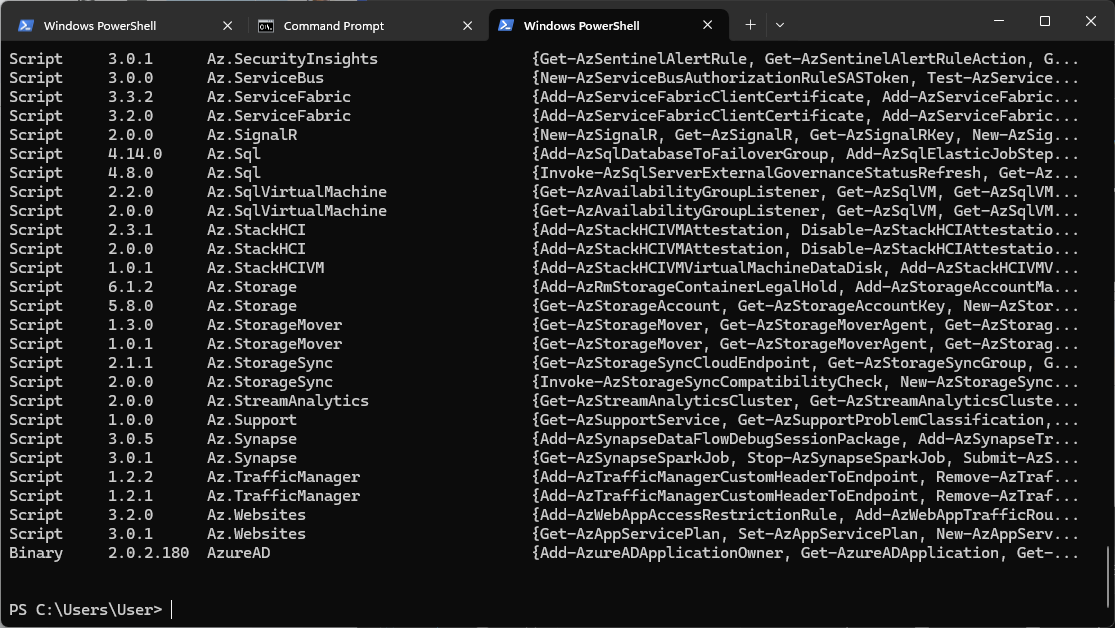
As you can see, all the commands are present, and you can now fully use the AZ module.
Understanding Authentication with Azure

What’s next, now that we’ve installed the AZ module? You need to remember that you have to authenticate first before you can execute any commands in Azure.
Authentication is always the first step in making changes to your tenant, even on the web portal.
The AZ module contains the Connect-AzAccount cmdlet, which allows you to use the command line to authenticate to the Azure tenant.
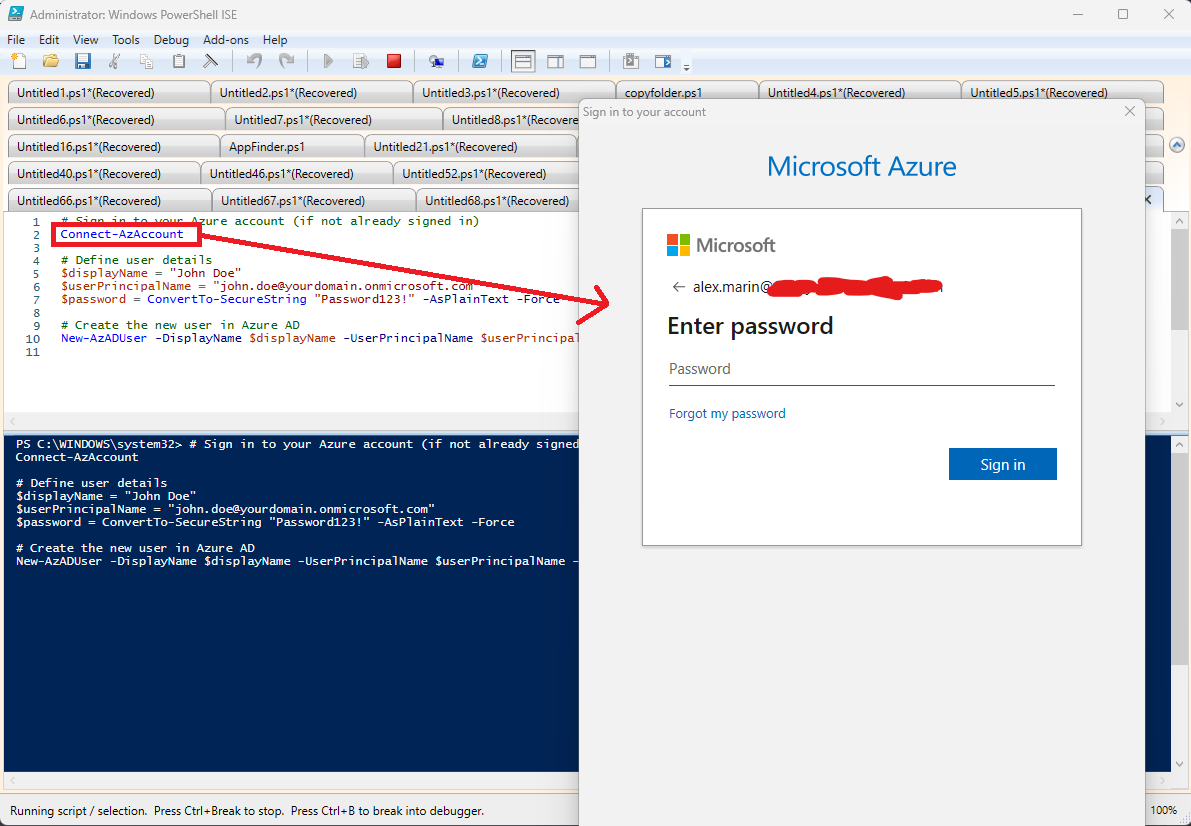
When you run the command, a login window will appear, asking you to enter your Azure credentials.
Once you successfully authenticate:
- You get a security token: This token works as a temporary pass that confirms your identity to the Azure services. This feature proves that you logged in successfully and also allows you to make calls to Azure and manage resources.
- A session starts: This isn’t just any session. It’s a secure link between your PowerShell and Azure, ensuring that the commands you run and the changes you make are securely communicated back and forth.
- Access boundaries are set: Depending on your account and permissions, you may have a wide range of capabilities or be limited to specific areas of Azure. It depends on what roles and access rights are associated with your account.
Remember that the token you get when you authenticate isn't permanent. It expires after a certain time for security reasons. This means you'll need to re-authenticate from time to time to keep your session active and secure.
Understanding Microsoft Graph

Microsoft Graph is at the heart of everything Microsoft 365-related, and it is a tool that allows you to get the data for all M365 services, including Office 365, Azure Active Directory, OneDrive, Azure, and more.
Microsoft Graph communicates through the REST (Representational State Transfer) API. REST APIs are a standard method for interacting with Web Services, and many companies and solutions use them.
If you want to see sample queries or just work with Microsoft Graph before jumping to PowerShell REST requests, you can go to the official Graph Explorer website, log in with your tenant credentials, and start exploring the different sample queries available.
For a list of all possible queries, simply run this query:https://graph.microsoft.com/v1.0/
The main methods of REST APIs are:
- GET: This method retrieves information from the specified source. For example, accessing `https://graph.microsoft.com/v1.0/me` would return information about the currently authenticated user. This is one method to read data without affecting what’s stored on the server.
- POST: It sends data to a server to create or update a resource. It’s often used for submitting form data or uploading a file.
- PUT: This method replaces all existing representations of the target resource with the uploaded content. Its purpose is to completely update the state of a resource.
- PATCH: Similar to PUT, PATCH applies partial modifications to a resource. It’s useful for updates where you only want to change specific fields without touching the rest.
- DELETE: As the name implies, this method deletes the specified resource.
These methods respond to standard CRUD (Create, Read, Update, Delete) operations, allowing you to manage data across all Microsoft services in a structured manner.
For example, when you request Microsoft Graph via REST API, you are sending a structured URL that specifies what you want to interact with, as well as an HTTPS method that defines the action that you want to perform.
A simple GET request to `https://graph.microsoft.com/v1.0/me` returns a JSON representation of the user profile associated with the authenticated user.

So, keep in mind that the data from the Microsoft Graph is returned in JSON format (JavaScript Object Notation).
JSON is a lightweight data-interchange format that's easy for humans to read and write and easy for machines to parse and generate.
It’s essentially a collection of name/value pairs and array data types, making it a universal language for the web APIs.
For example, a simple GET request to `https://graph.microsoft.com/v1.0/me` may return something like this:
{
"displayName": "John Doe",
"jobTitle": "Software Developer",
"mail": "johndoe@example.com",
"id": "12345678"
}Understanding Connect-MgGraph cmdlet

The Connect-MgGraph cmdlet is part of the Microsoft Graph PowerShell SDK, which allows you to call Microsoft Graph APIs directly from PowerShell scripts.
However, before we can use this cmdlet, we need to have the Microsoft.Graph.Authentication module installed. This is similar to the AZ module, but first we must install it with this command line inside an elevated PowerShell instance:
Install-Module -Name Microsoft.Graph.Authentication
Now that it’s installed, we can use the Connect-MgGraph cmdlet. Once this is executed, a sign-in page similar to the AZ module will appear, asking you to enter your credentials.
One of the powerful features of `Connect-MgGraph` is the ability to specify scopes. Scopes define your connection’s permissions, which limit the data and actions your scripts can access and perform on Microsoft Graph.
For example, if you're working with user data, you could use the `User.Read.All` scope. This granularity ensures that your scripts do what they're supposed to do, enhancing security and compliance.
Connect-MgGraph -Scopes "User.Read.All", "Mail.Read"
In this command, we connect to Microsoft Graph with the permission to read all user profiles and their mail. The exact scopes you'll need depend on the tasks your script is performing.
Since we are working with the applications side, we need the DeviceManagementApps.Read.All and DeviceManagementApps.ReadWrite.All scopes, so our command would be:
Connect-MgGraph -Scopes "User.Read.All", "Group.ReadWrite.All", "DeviceManagementApps.Read.All", "DeviceManagementApps.ReadWrite.All"
After successfully running Connect-MgGraph, your PowerShell session is authenticated with Microsoft Graph, and you're ready to start making API calls.
Your session will include the authentication token, allowing you to fetch data, manage resources, and execute actions across the Microsoft ecosystem, all from your PowerShell prompt.
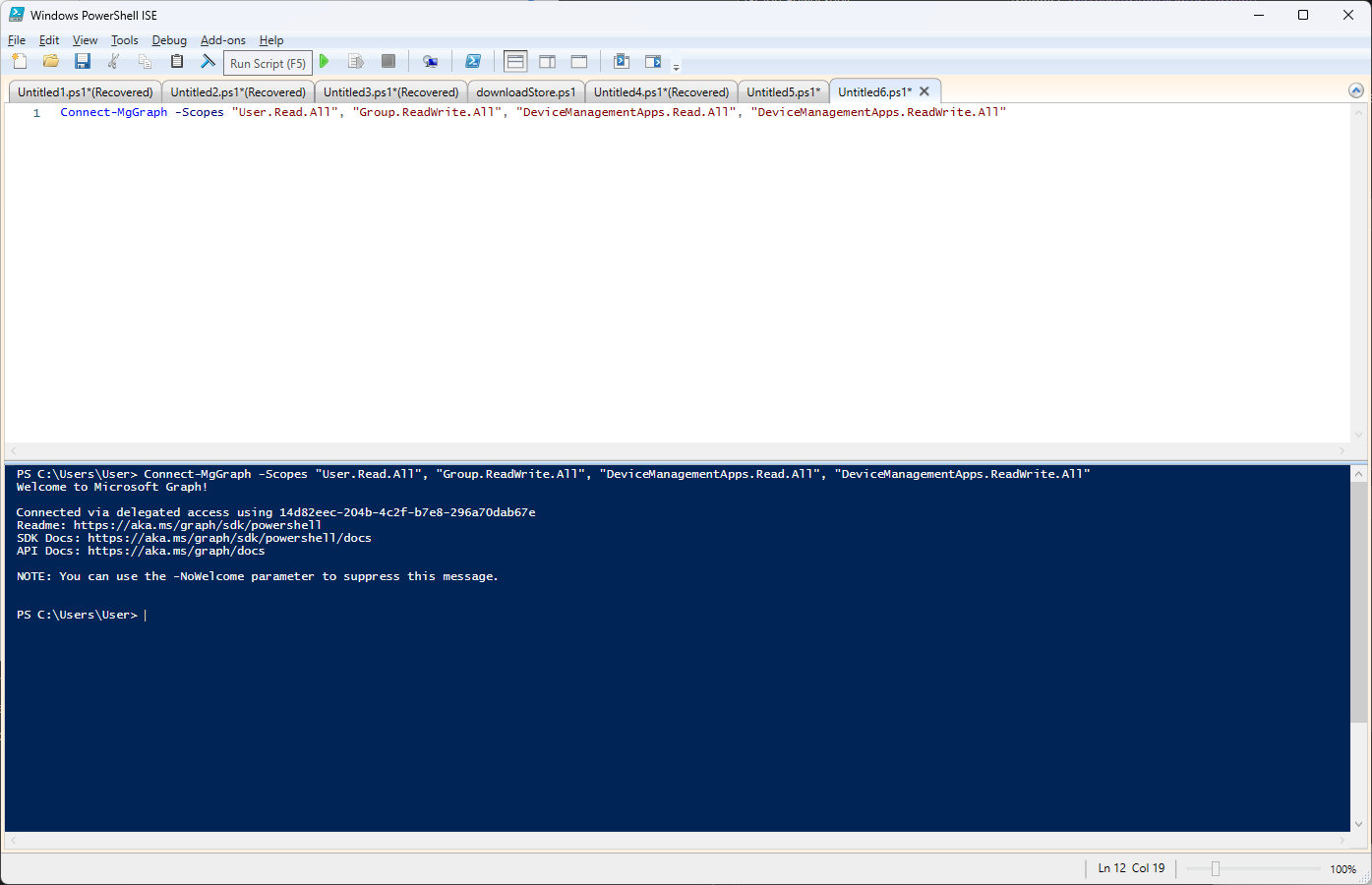
`Connect-MgGraph` is more than just a login step. It sets the stage for secure, controlled interactions with Microsoft's cloud services.By specifying scopes, you're tailoring the session to the needs of your script, ensuring that you have only the right level of access needed to get the job done without oversharing permissions. It's an important step in building PowerShell scripts that interact with Microsoft services efficiently and securely.
Understanding Invoke-MgGraphRequest cmdlet

After connecting with the Connect-MgGraph cmdlets, the next step is to understand how Invoke-MgGraphRequest works.
Invoke-MgGraphRequest is the primary tool for sending HTTPS requests to Microsoft Graph. With it, you can execute commands that directly affect your Microsoft 365 environment.
Whether you’re pulling user lists, updating calendars, managing devices, or doing any other tasks, the cmdlet `Invoke-MgGraphRequest` communicates your requirements to Microsoft Graph.
The beauty of `Invoke-MgGraphRequest` lies in its flexibility. You specify the HTTPS method (GET, POST, PATCH, DELETE, PUT) to match the action you want to perform.
Then you provide the endpoint URL for the resource you’re targeting, as well as any necessary headers or body content for the request.
Let’s say you want to retrieve details about your user. You’d make a GET request like this:
Invoke-MgGraphRequest -Method GET -Uri "https://graph.microsoft.com/v1.0/me"

Get all Win32 Apps from Intune via PowerShell

So now we know what Azure is, how to access it with the PowerShell AZ module, what Microsoft Graph is, and how to access data with the Graph module within PowerShell.
Next, we’ll look at how we can put all these pieces together and use PowerShell to get the Win32Apps from Intune.
Assuming we are given the task to manage the applications within your organization, we would need a neat way to list all of the Win32 Applications within your Intune tenant. This process involves connecting to Microsoft Graph, fetching a list of apps, and then processing the data to focus only on the Win32 apps.
Here’s how you would approach this task, broken down into actionable steps that use the cmdlets and concepts we went over:
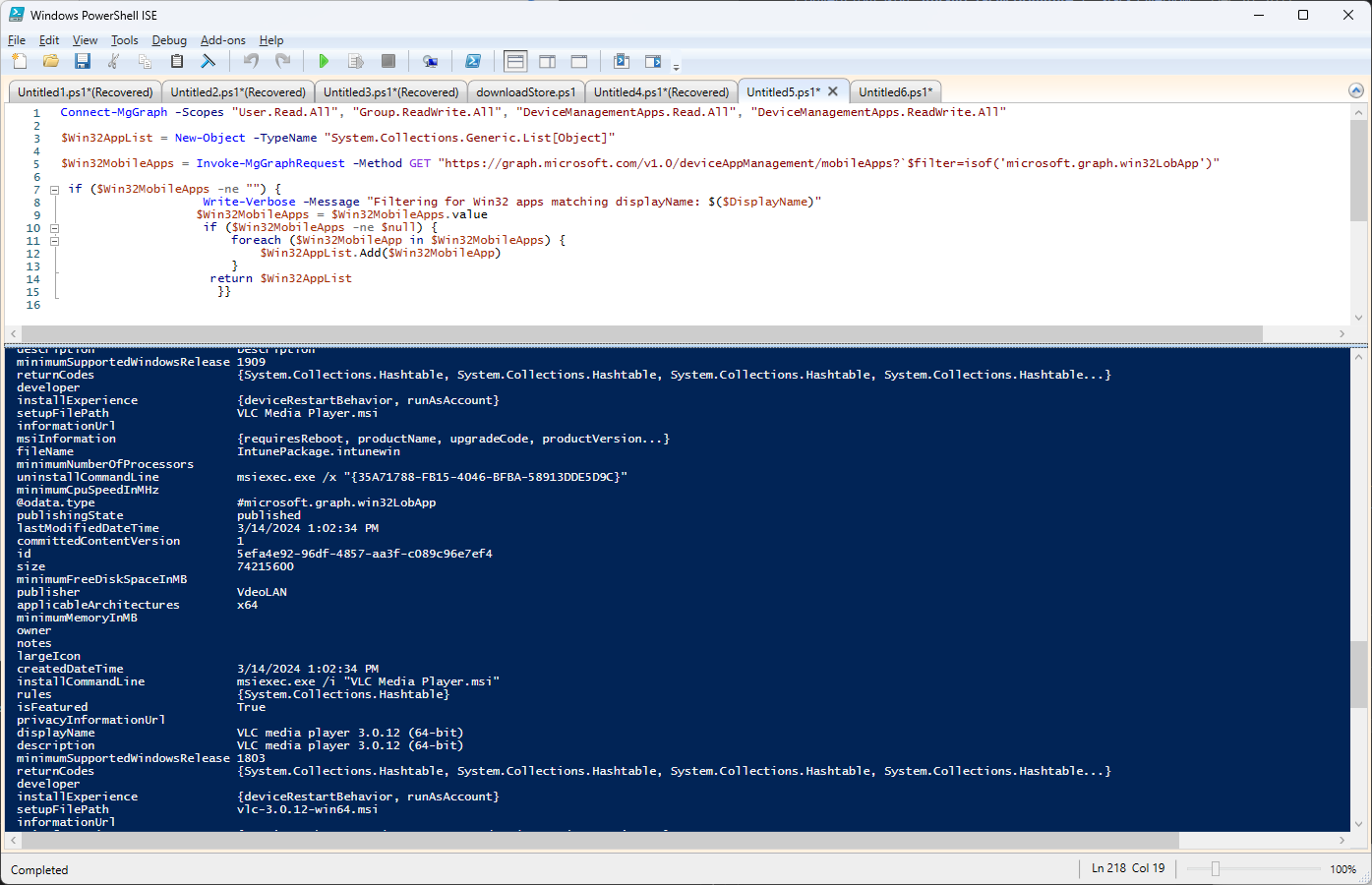
1. Authenticate Your Session: First, use `Connect-MgGraph` to authenticate your session. This step checks that you have the necessary permissions to access application information within your tenant.
Connect-MgGraph -Scopes "User.Read.All", "Group.ReadWrite.All", "DeviceManagementApps.Read.All", "DeviceManagementApps.ReadWrite.All"
2. Retrieve Application Data: With your session authenticated, use `Invoke-MgGraphRequest` to get a list of all mobile apps managed by Intune, filtering specifically for Win32 apps:
$Win32MobileApps = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/v1.0/deviceAppManagement/mobileApps?`$filter=isof('microsoft.graph.win32LobApp')"3. Process and Filter Data: This GET request fetches all mobile apps, then filters them to only include Win32 Line of Business (LOB) apps.
We also need to create an object where we keep all the parsed data:
$Win32AppList = New-Object -TypeName "System.Collections.Generic.List[Object]"
We parse the response from Microsoft Graph to inspect or manipulate the data. In this case, you could iterate through the list of apps, extracting relevant details such as name, publisher, and version.
if ($Win32MobileApps -ne "") {
Write-Verbose -Message "Filtering for Win32 apps matching displayName: $($DisplayName)"
$Win32MobileApps = $Win32MobileApps.value
if ($Win32MobileApps -ne $null) {
foreach ($Win32MobileApp in $Win32MobileApps) {
$Win32AppList.Add($Win32MobileApp)
}
return $Win32AppList
}}This script returns a clear, concise list of all Win32 applications managed by Microsoft Intune, along with their key attributes.
Final Takeaways

- PowerShell becomes far more useful once it is paired with the Az and Graph modules for real automation
- Authentication is always the first gate you must pass before touching anything in Azure or Microsoft 365
- REST methods shape every interaction with Graph and learning them early removes a lot of confusion later
- JSON output is the language of Microsoft Graph and understanding its structure helps you script with confidence
- The Az module gives you direct control over Azure resources from a command line instead of relying on the portal
- Connect-MgGraph sets the permissions that define exactly what your session can access
- Invoke-MgGraphRequest is the engine that sends your requests and retrieves the data you ask for
- Filtering Win32 applications becomes a focused task once you know how to collect and process Graph output
- Scripts built on authenticate query and parse create a repeatable pattern for everything in Microsoft 365
- Automation with Graph and PowerShell reduces manual effort and builds a cleaner and more reliable management workflow
Conclusion

Putting everything together in this manner brings out the practical value that PowerShell and Microsoft Graph deliver when managing Microsoft 365 services.
Automating tasks that usually feel tedious and time-consuming gives you genuine chances to save time, reduce errors, and increase the efficiency of your IT operations.
This example also draws attention to a structured way of problem-solving with PowerShell and Microsoft Graph: authenticate, request, and process. Any IT professional using Microsoft 365 can use this framework as a flexible toolkit for a wide range of tasks beyond application management.
This powerful approach includes automating your work with Win32 applications.
In other words, using PowerShell and Microsoft Graph to automate and manage tasks for Microsoft 365 involves more than just scripts, as it’s about making your workflows seamless, enhancing your IT processes, keeping the management tasks much more manageable, and opening your time for more strategic initiatives.
This example of managing Win32 apps in Intune is just one of the endless examples that open up when you combine PowerShell's scripting power with Microsoft Graph's extensive API capabilities.
