How to digitally sign an MSI installer using different methods
Ensuring the security and integrity of software applications is a key part of modern digital safety practices. Digitally signing an MSI file from the command line is a straightforward process that enhances the security and trustworthiness of your application.
This article simplifies the process of applying digital signatures to MSI files by demonstrating various methods, including command lines, PowerShell, and signing tools, while also offering insights into an alternative graphical approach using Advanced Installer's user interface.
Prerequisites for Digital Signing MSI Files

Before starting, ensure you have a valid code signing certificate from a trusted certificate authority (CA) or generate a self-signed certificate.
For more details on PFX, check out our blog article "What is a Code Signing Certificate and How to Ensure Digital Trust for Your Application," where we dive deeper into the topic.
Remember to export your certificate to a PFX file format and keep the password handy. A Personal Information Exchange (.pfx) file is a password-protected certificate commonly used for code signing your application. It derives from the PKCS 12 archive file format certificate, and it stores multiple cryptographic objects within a single file.
Check out our blog post "What is a PFX Certificate and How to Generate It" for a more in-depth look at PFX.
Digitally Sign Your MSI File using Microsoft SignTool

SignTool is Microsoft’s native digital signature tool, available within the Windows SDK, which can be downloaded from here.
After downloading the SDK, proceed with the install wizard and select the SignTool as the feature to install, as shown below.
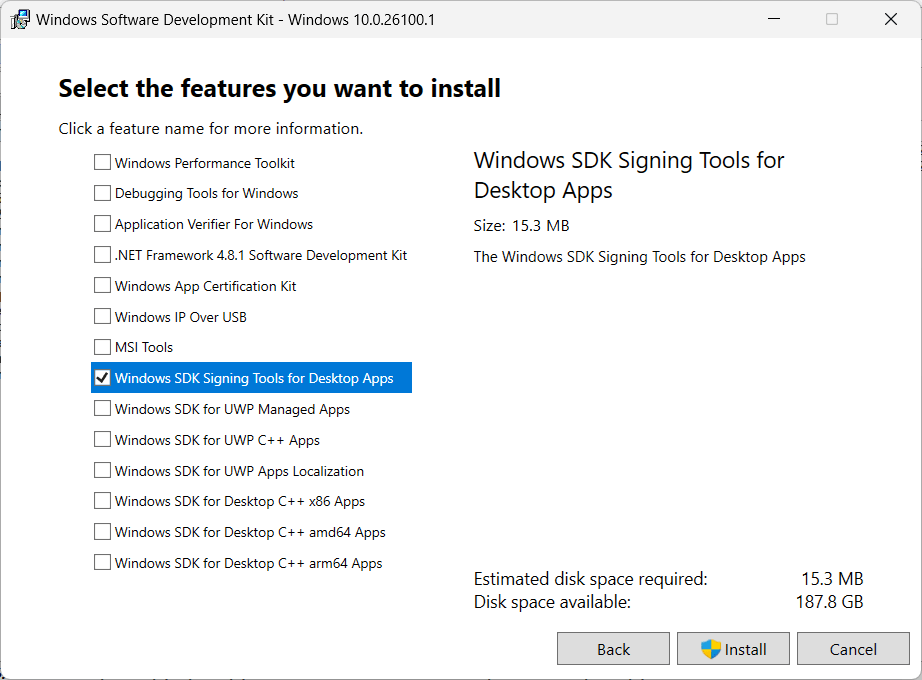
Once the installation is complete, download the purchased certificate (usually in a .pfx format) and install it on your machine in the local Windows Certificate Store.
Now, we are ready to begin the signing process.
Open a command prompt as an administrator and run the following command:
signtool sign /f "[path to your cert]\certificate.pfx" /p "yourpassword" /fd SHA256 /t http://timestamp.digicert.com "[path to your msi]\installer.msi"
Here are the switches used
- /f - the path to the .pfx file containing your certificate.
- /p - the password for the certificate file. (You can skip this one if there is no password for the certificate)
- /fd - algorithm to use (SHA256 is recommended).
- /t - URL of the timestamp server (in case you opted for an Extended Validation certificate).
You can check the success of the signature using the following command:
signtool verify /pa "[path to your msi]\installer.msi"
Digitally Sign Your MSI File via CA Website or Tool

There are some Certified Authority (CA) or retail vendors who offer online sign tools.
Once you buy the CA, there should be an option in your account on the vendor's site where you can upload your MSI file for signing and then get the download link to the signed MSI.
Keep in mind that the size of the MSI might limit this method and you will not be able to “online” digitally sign your installer if it’s larger.
Alternatively, some vendors provide a tool that you can install on your computer, which performs the same signing process.
This method varies depending on the vendor, so it's important to consult the help section and guidelines provided on the website where you purchased the certificate.
Digitally Sign Your MSI File from the Command Line Using PowerShell

To digitally sign an MSI file from the command line, we’ll use the PowerShell Set-AuthenticodeSignature cmdlet.
The Set-AuthenticodeSignature cmdlet is a PowerShell command that applies a unique digital signature to files, including executables (EXE files), dynamic-link libraries (DLL files), MSI files, scripts, and more.
To digitally sign an MSI file, you'll need to specify the path to the file you want to sign using the -FilePath parameter and the code signing certificate using the -Certificate parameter.
Here’s how you can accomplish this using the PowerShell Set-AuthenticodeSignature cmdlet:
1. Open PowerShell with administrative privileges.
2. Securely store the certificate password by converting the certificate password into a secure string:
$certificatePassword = ConvertTo-SecureString -String "YourCertificatePassword" -Force -AsPlainText
3. Specify the path to your certificate:
$certificatePath = "C:\Path\To\YourCertificate.pfx"
4. Create an instance of the certificate object and import the certificate:
$certificate = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2 $certificate.Import($certificatePath, $certificatePassword, [System.Security.Cryptography.X509Certificates.X509KeyStorageFlags]::Exportable)
5. Specify the path to your MSI file:
$msiFilePath = "C:\Path\To\YourFile.msi"
6. Apply the digital signature to the MSI file using the provided certificate:
Set-AuthenticodeSignature -FilePath $msiFilePath -Certificate $certificate
7. Check the digital signature information of the MSI file to verify if the signing was successful:
Get-AuthenticodeSignature -FilePath $msiFilePath
Digitally Sign Your MSI File Using Advanced Installer’s GUI

Alternatively, Advanced Installer's GUI simplifies the digital signing process by integrating signtool.exe, eliminating the need for command-line operations. This functionality is designed to save time and streamline the signing process.
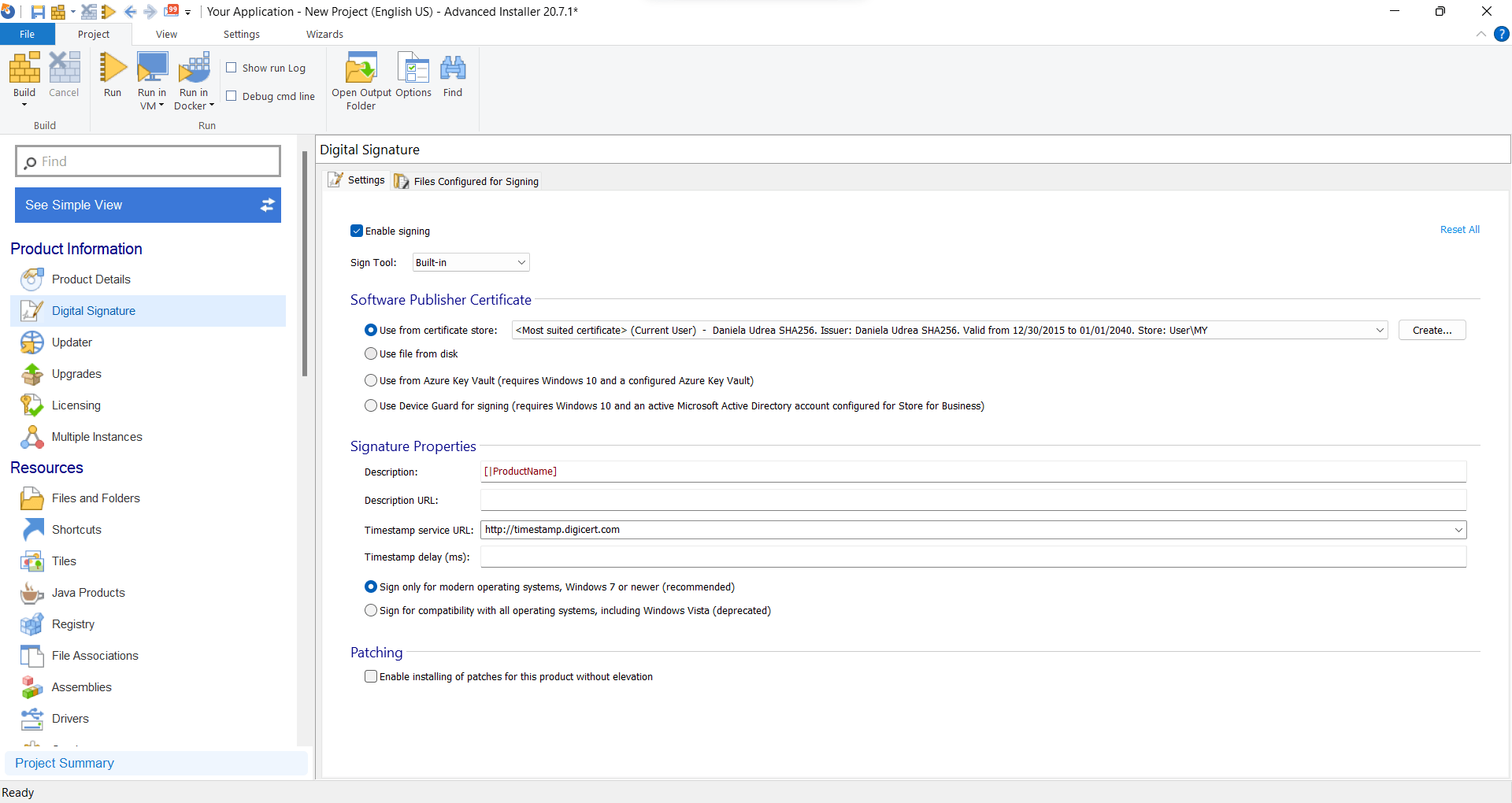
Experience Advanced Installer's digital signing capabilities firsthand with its 30-day free full-feature trial.
Start Free Trial
Video Tutorial Available

Stay Ahead of the Curve in Application PackagingTo keep up with more insights and trends in software packaging and deployment, subscribe to our newsletter. Get the latest updates and expert advice delivered right to your inbox.Subscribe to Our Newsletter
