PowerShell & Intune, Automate your Work - Part 3: Manage Win32 App Dependencies
Welcome back to our series on automating Intune operations with PowerShell. If you've been following along, you know we've covered quite a bit— from the basics of setting up and authenticating with the AZ Module, to retrieving and managing Win32 applications, and diving into application assignments.
Today, we're rolling up our sleeves to tackle another crucial piece of the app management puzzle: Win32 App Dependencies.
Ever wondered how some applications refuse to play nice unless they get their favorite buddies installed first? That's where understanding dependencies comes into play.
PowerShell combined with Microsoft Graph API can help us manage these dependencies efficiently.
In this third part of our series:
- We will explore how to retrieve these dependencies directly through the power of scripts.
- We will break down a script that not only fetches the Win32 applications but also examines their interconnections, ensuring a smooth deployment and management experience.
Recap of Part 1 and Part 2

Before we proceed with some new scripts, let's review what we’ve covered so far.
In the first part of our series, we used the AZ Module to connect to Azure and retrieve Win32 apps from Intune.
This was more than just a simple retrieval; it was about understanding the landscape of applications that many organizations depend on daily.
We learned how to use Invoke-MgGraphRequest, a powerful cmdlet that interacts directly with Microsoft Graph API, to pull detailed information about these applications, setting the stage for more complex operations.
In part two, we stepped up our game by fetching assignment details for those apps, using the same PowerShell cmdlets, but with a different approach. We explored how applications are assigned within Intune and the implications of these assignments on network and device management.
By refining our PowerShell scripting techniques, we could fetch the list of Win32 apps and retrieve detailed assignment information for each app. This allowed us to see not just what apps were deployed, but also how they were configured across different user groups and devices.
Understanding these assignments was crucial for ensuring that the right tools were available to the right parts of the organization, enhancing productivity and ensuring compliance.
Retrieve Win32 App Dependencies in Intune using PowerShell

Application dependencies in Microsoft Intune are essential for managing application installations across your organization's devices.
These dependencies ensure that certain prerequisite applications are installed before or alongside a target application, which helps maintain system stability and functionality.
In Intune, an application dependency means that one application must be present on the device for another application to function correctly or to install properly.
This relationship is crucial in scenarios where software requires specific libraries, frameworks, or other supporting software to be present. For instance, a complex accounting software might require a specific version of .NET Framework or a database engine installed before it can run.
Dependencies are not limited to prerequisites; they can also dictate the order in which applications should be installed, ensuring that all required components are set up in a sequence that avoids conflicts and errors.
Now, let’s get to the main task: retrieving dependencies for our Win32 apps using PowerShell.
Here’s a detailed breakdown of the script:
Connect-MgGraph -Scopes "User.Read.All", "Group.ReadWrite.All", "DeviceManagementApps.Read.All", "DeviceManagementApps.ReadWrite.All", "GroupMember.Read.All", "Directory.Read.All", "Directory.ReadWrite.All", "Group.Read.All"
As with our part two, we start by connecting to Microsoft Graph using specific scopes necessary for accessing detailed app data.
These scopes include:
- "User.Read.All"
- "Group.ReadWrite.All"
- "DeviceManagementApps.Read.All"
- "DeviceManagementApps.ReadWrite.All"
- "GroupMember.Read.All"
- "Directory.Read.All"
- "Directory.ReadWrite.All"
- "Group.Read.All"
$Win32MobileApps = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/v1.0/deviceAppManagement/mobileApps?$filter=isof('microsoft.graph.win32LobApp')"Next, we'll issue a call to grab all mobile apps classified as win32LobApp.
We're using the stable v1.0 endpoint for this request because it's just a simple list of apps.
if ($Win32MobileApps -ne "") {
$Win32MobileApps = $Win32MobileApps.value
if ($Win32MobileApps -ne $null) {
foreach ($Win32MobileApp in $Win32MobileApps) {
$Win32MobileApps2 = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/beta/deviceAppManagement/mobileApps/$($Win32MobileApp.id)/relationships"
if ($Win32MobileApps2.value -ne $null) {
if ($Win32MobileApps2.value.'@odata.type' -like "#microsoft.graph.mobileAppDependency") {
return $Win32MobileApps2.value
}
}
}
}
}After collecting the list of apps, we go through them one by one, checking out their relationships.
This part becomes interesting because we're using the beta endpoint. Why beta, you ask?
Because the regular v1.0 endpoint does not currently provide us with useful relationship information. We are specifically looking for entries with a mobileAppDependency. These dependencies function similarly to the strings that connect various apps, indicating which apps must be installed first or simultaneously.
Here’s the full code for this operation:
Connect-MgGraph -Scopes "User.Read.All", "Group.ReadWrite.All", "DeviceManagementApps.Read.All", "DeviceManagementApps.ReadWrite.All", "GroupMember.Read.All", "Directory.Read.All", "Directory.ReadWrite.All", "Group.Read.All"
$Win32AppList = New-Object -TypeName "System.Collections.Generic.List[Object]"
$Win32AppAssignmentList = New-Object -TypeName "System.Collections.Generic.List[Object]"
$Win32MobileApps = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/v1.0/deviceAppManagement/mobileApps?`$filter=isof('microsoft.graph.win32LobApp')"
if ($Win32MobileApps -ne "") {
$Win32MobileApps = $Win32MobileApps.value
if ($Win32MobileApps -ne $null) {
foreach ($Win32MobileApp in $Win32MobileApps) { $Win32MobileApps2 = Invoke-MgGraphRequest -Method GET "
https://graph.microsoft.com/beta/deviceAppManagement/mobileApps/$($Win32MobileApp.id)/relationships
"
if ($Win32MobileApps2.value -ne $null) {
if ($Win32MobileApps2.value.'@odata.type' -like "#microsoft.graph.mobileAppDependency") {
return $Win32MobileApps2.value
}
}
}
}}
This script will output all the applications are marked as dependencies in the environment:
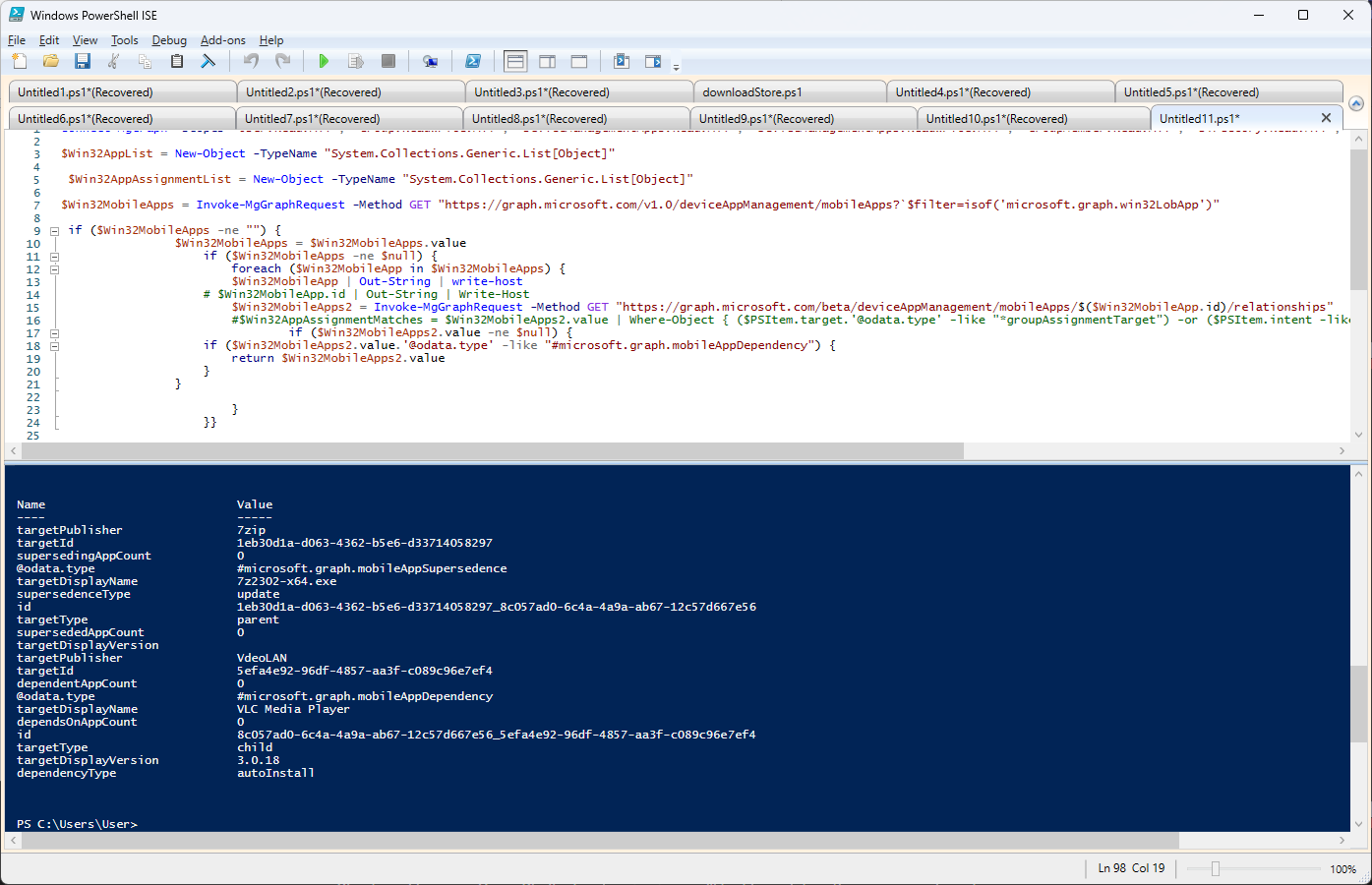
Retrieve Win32 App Dependencies for a Particular Application

If you only want to find the dependencies for a specific application based on the DisplayName, the script can be easily adapted. All you need to do is check if:
if($Win32MobileApp.displayName -like "*7z*"){Adding this line to the code will filter the results to only show dependencies for the specified app.

The full modified code for searching the dependencies of a particular app in Intune with PowerShell is:
Connect-MgGraph -Scopes "User.Read.All", "Group.ReadWrite.All", "DeviceManagementApps.Read.All", "DeviceManagementApps.ReadWrite.All", "GroupMember.Read.All", "Directory.Read.All", "Directory.ReadWrite.All", "Group.Read.All"
$Win32AppList = New-Object -TypeName "System.Collections.Generic.List[Object]"
$Win32AppAssignmentList = New-Object -TypeName "System.Collections.Generic.List[Object]"
$Win32MobileApps = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/v1.0/deviceAppManagement/mobileApps?`$filter=isof('microsoft.graph.win32LobApp')"
if ($Win32MobileApps -ne "") {
$Win32MobileApps = $Win32MobileApps.value
if ($Win32MobileApps -ne $null) {
foreach ($Win32MobileApp in $Win32MobileApps) {
if($Win32MobileApp.displayName -like "*7z*"){
$Win32MobileApps2 = Invoke-MgGraphRequest -Method GET "https://graph.microsoft.com/beta/deviceAppManagement/mobileApps/$($Win32MobileApp.id)/relationships"
if ($Win32MobileApps2.value -ne $null) {
if ($Win32MobileApps2.value.'@odata.type' -like "#microsoft.graph.mobileAppDependency") {
return $Win32MobileApps2.value
}
}
}
}
}}Conclusion

So there you have it! That concludes our trip through the script for today. We connected to Microsoft Graph, retrieved a list of apps, and identified all of their dependencies.
Each line of this script serves as a step deeper into understanding and managing dependencies.
By comprehending and controlling these dependencies, you can ensure smoother deployments and more stable applications across your organization’s devices.
Stay tuned for more insights and scripts to streamline your Intune management with PowerShell!
Subscribe to our blog to stay updated with the latest tips and tutorials.
