Edit Firewall Exception Dialog


Direction

Specify what type of traffic do you want your firewall rule to allow or block.
Display Name

Specify the name of the firewall exception rule that will be visible in the Windows Firewall Configuration Manager. This string is localizable.
Group

Bundle the rule in the specified group. Performing operations at the group level will activate or deactivate all contained application exceptions.
This functionality is available for installers running on Windows Vista SP1 or
later.
Program path

Specify the process path that should be authorized / registered with Windows Firewall.
During installation, the formatted value specified in this field must expand to a
valid file path that exists on disk.
Protocol

Specify the network protocol for the chosen port.
Port number

Specify the port number to authorized / registered with Windows Firewall. Multiple ports must be written comma-separated (e.g. 2050, 2055, 2057) and port ranges must be written hyphenated (e.g. 2050-2057).
During installation, the formatted value specified in this field must expand to a
valid port number.
Condition

You can condition the configuration of this firewall exception.
Action

Specify what action should be taken when a connection matches your conditions.
Network Scope

Click the Network Scope link button and specify the network scope for which this firewall exception applies.
Network Profile

Click the Network Profile link button and select the network profiles to which the firewall exception will be added to.
All fields are of Formatted Type and can be edited using Smart Edit Control.
When the Windows Firewall service is turned off the installation of the firewall
exception rules will be skipped.
Edit Firewall Exception Scope Dialog

Configure the network scope for which the firewall rule applies. You have the following options:
- Any computer
- Local network (subnet) only
- Custom IP / Subnet mask list
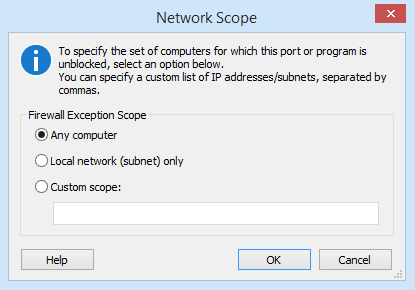
The custom scope list consists of one or more comma-delimited tokens specifying the remote addresses from which the application can listen for traffic.
The subnet may be specified using either a subnet mask or network prefix notation. If neither a subnet mask nor a network prefix is specified, the subnet mask defaults to 255.255.255.255. Examples of valid subnets: 10.0.0.2/255.0.0.0; 10.0.0.2/8; 10.0.0.2.
You can specify an IPv4 / IPv6 address range in the format "start
address - end address".
Firewall Profile Dialog

The network profiles set the appropriate firewall settings and security setting based on the type of network that you connect to. You can enable Advanced Installer to add a new firewall exception to a specific network profile.

Active profile

If this option is selected, the firewall exception will be added to the currently active network profile.
Specific profile

If this option is selected you can specify the network profiles for which the firewall exception will be added. You can select any combination made from the three profiles.
Domain

If this option is selected the firewall exception will be added to the "Domain" network profile. This profile is specific to enterprise workplaces and the network location is controlled by the network administrator.
Private

When this option is selected the firewall exception will be added to the "Home" and "Work" network profiles. These profiles are specific to private locations where all the devices from the network are trusted and therefore the network discovery is set the on.
Public

When this option is selected the firewall exception will be added to the "Public" network profile. This profile is specific to public places and therefore network discovery is set to off to prevent the computers from any mallware.
The Private, Public, Domain network
profiles exist only on Windows Vista and above. On older
operating systems only the Active network profile
exists and can be configured.
If you are installing a package on an older OS that was configured to
add firewall exceptions to "Public, Private" or "Domain" profiles they
will be added to the "Active" profile.